The first part of this blog series was dedicated to the log management software Graylog. We successfully configured the first input via the web interface of Graylog and defined the data transmission of the system log in the MUC.easyplus.
This lay the foundations of this blog post where we demonstrate how to generate alarm messages for certain events captured in the system log.
In the third part we will configure an e-mail notification.
As error scenario we pick an erroneous login as Root, which can be caused by typos, but also by a hacking attack and thus by an unauthorized attempt to access the device.
To configure the alarm, log in as admin on the Graylog homepage and navigate to “Alerts”.
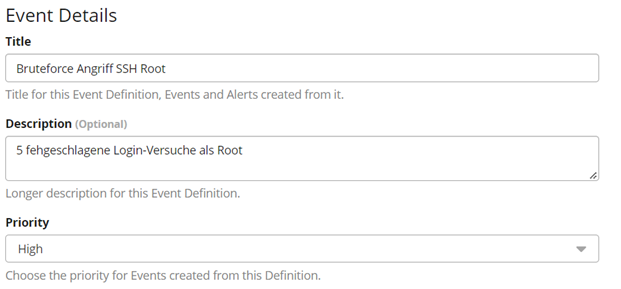
Event Details
Now click on “Get Started!”. In the first section “Event Details”, general aspects like a title for the alarm, a description and the priority can be configured. The priority is classified to “high” as it is a potential security breach and an unauthorized access on the device in this case.
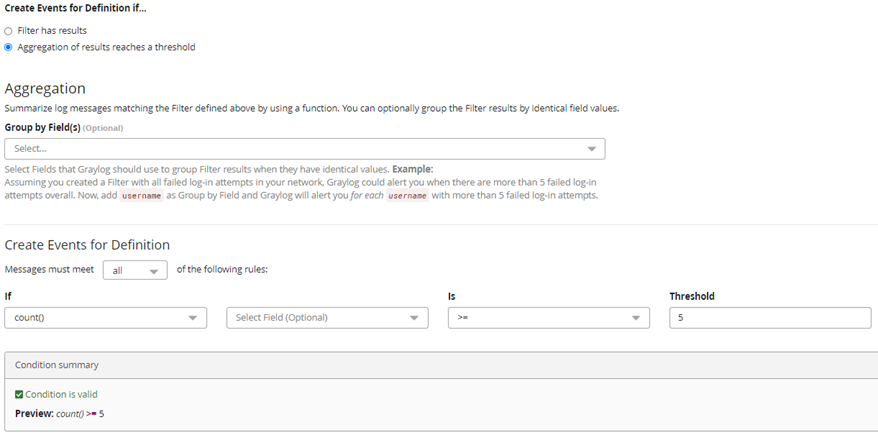
Filter & Aggregation
After clicking “Next”, the section “Condition” opens. Without a licence, only “Filter & Aggregation” can be selected under “Condition Type”. The configuration of the alarm follows.
Now the question arises for what and in which time window Graylog is to screen the system log to generate a message.
This requires knowing the system log. For that, log in as admin per SSH, type in incorrect access data for the user Root and inspect the incoming messages in the Tab “Log” of the MUC.easyplus.
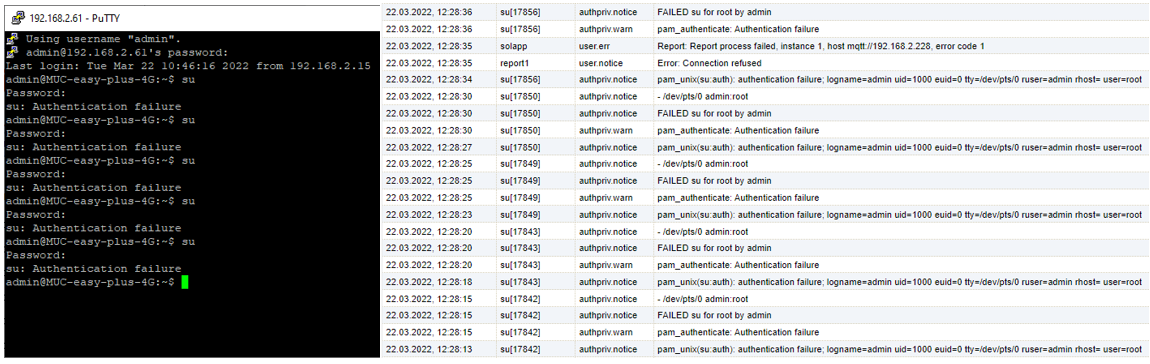
The message is as follows:
pam_unix(su:auth): authentication failure; logname=admin uid=1000 euid=0
tty=/dev/pts/0 ruser=admin rhost= user=root
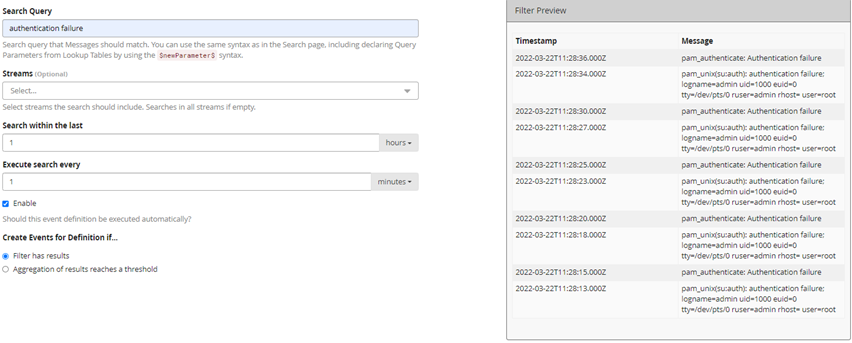
For the first parameter “Search Query” you can type the term to search for. In this case, we opt for a search for “authentication failure”. Very helpful in this regard is the Filter Preview in the right pane of the window. As the preview is void at first, the parameter “Search within the last” is set to 1 hour. Then the filtered messages are displayed.
These are still quite unspecific, as the terms “authentication” and “failure” are also part of unrelated messages. We strive to search for the string “authentication failure”. The search term must be surrounded by quotation marks. As we are interested in login-attempts of the user Root, this first search is combined with the second search. We insert “user=root” and combine both searches with a logical AND: “authentication failure” && “user=root”.
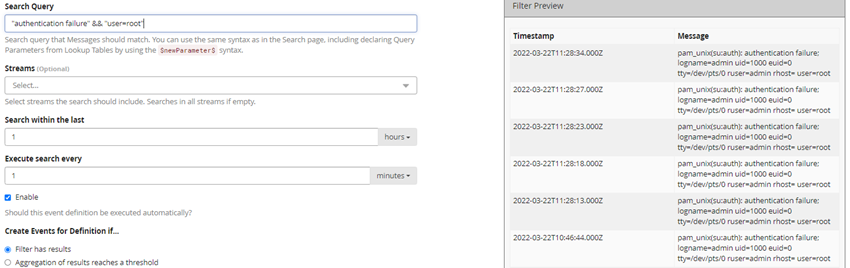
It was successful. Perfect!
Finally, the time window needs to be defined, to a search once per minute within the last 5 minutes. In the lower area we set that a message is to be generated if the event occurs 5 times.
Fields
In this particular case, the section “Event fields” is skipped. This can turn out useful if many alarms can be assigned to an event.
This was the last step to generate and define an alarm. Thus, the log is first filtered for certain conditions and the alarm generated.
In the next step we want to be automatically notified if an alarm was detected. For simplicity this will be an e-mail notification.
In the third part of this blog series, we will shed light on defining the e-mail notification.


